If you landed on this page you are probablly working on packaging Microsoft Teams and have been banging your head against a desk trying to figure out how to disable it from loading at startup. Fortunately for you, I figured out a solution that works 100% of the time.
What do you need?
Node.JS
Microsoft Teams
Notepad++
Where to download?
Node.JS – https://nodejs.org/en/
Microsoft Teams – https://teams.microsoft.com/downloads
Notepad++ – https://notepad-plus-plus.org/
Brief background
Essentially, Microsoft Teams is a webpage in the background. It was developed with Electron which is a framework that lets developers create cross-platform desktop apps with web front-end technologies. Some other popular applications such as Skype, and Visual Studio Code were also built with using this technology.
With Electron apps, most of the source files for the application will be packaged into a file named app.asar. You can open the file in Notepad but you cannot save it since it is a READONLY file. From my experience, any changes made to it via Notepad will crash the app and prevent it from loading.
How do you do it?
- Download and install Microsoft Teams
- Download and install Node.JS
- Open the CMD prompt as an Administrator
- Run:
npm install -g asar
- Run:
asar extract "%LOCALAPPDATA%\Microsoft\Teams\current\resources\app.asar" C:\Temp\asar
Note – Try running “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Node.js\Node.js command prompt.lnk” if the command prompt does not recognize the ASAR command.
- Navigate to C:\Temp\asar\lib
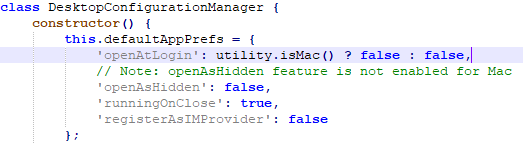
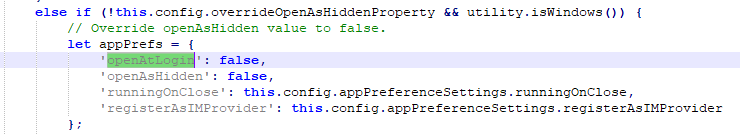
- Locate desktopConfigurationManager.js and open the file with Notepad++
- Search for OPENATLOGIN (There should be two references) and set the value to FALSE as shown below in the screenshots:
 li>
li>
Last but not least, it is time to repackage everything!
- Run:
asar pack "C:\TEMP\asar" "C:\TEMP\app.asar" --unpack *.node
Now that you have a customized app.asar, you can silently install Teams and also not worry about it launching at startup. See the install script below for an example:
# Install Microsoft Teams
Start-Process "$PSScriptRoot\Teams_windows_x64.exe" -ArgumentList "-s" -Wait
# Copy customized app.asar
Copy "$PSScriptRoot\app.asar" "$env:LOCALAPPDATA\Microsoft\Teams\current\resources\app.asar" -Force


 li>
li>